Navigating the cyber-risk landscape in the age of remote working
HLB Cybersecurity Report 2020
Navigating the cyber-risk landscape in the age of remote working
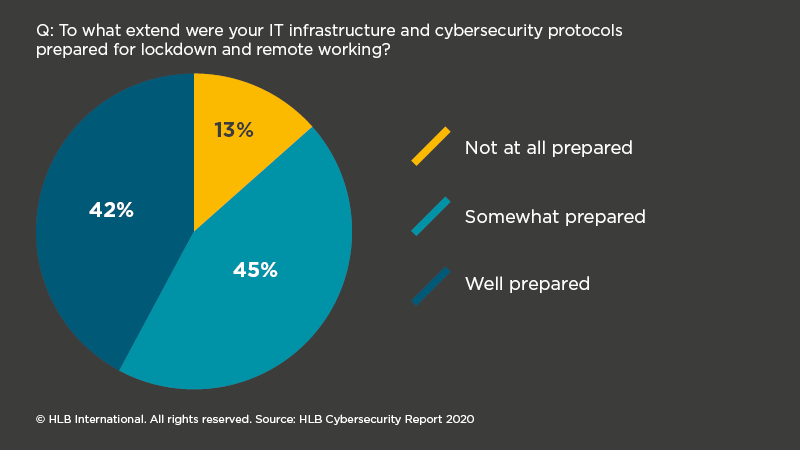
The COVID-19 pandemic forced many organisations across the globe to adopt remote working and digital processes with record speed. In doing so, CTOs and IT management faced increased vulnerabilities allowing for cyber-attacks and data breaches to take place more easily. Overnight, organisations went from controlled office environments to diverse home worksites. Continuing business, while securing multiple virtual environments, proved to be a challenge. But remote working is here to stay, so enterprises must adjust and overcome security hurdles.
In light of Cybersecurity Awareness Month 2020, we surveyed 76 IT professionals about their perceptions on information security and data protection in today’s complex digital environment. We also spoke with HLB cybersecurity experts about today’s cyber-risk landscape, the lessons learned from lockdown and the road ahead for CTOs to protect against cyber-crime in the age of remote working.
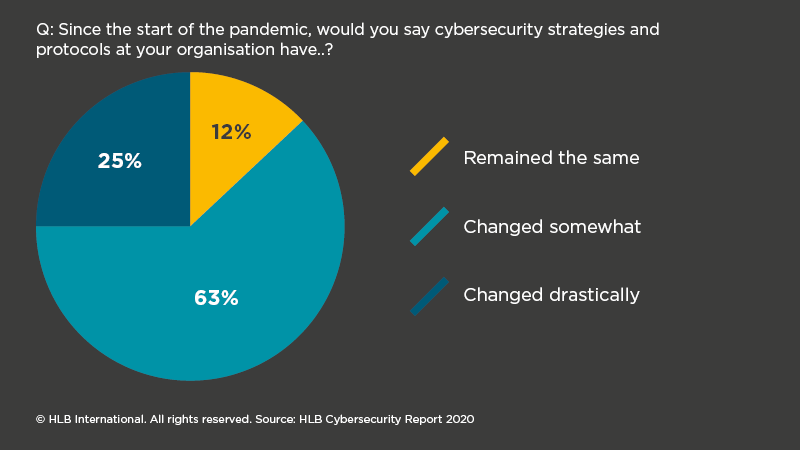
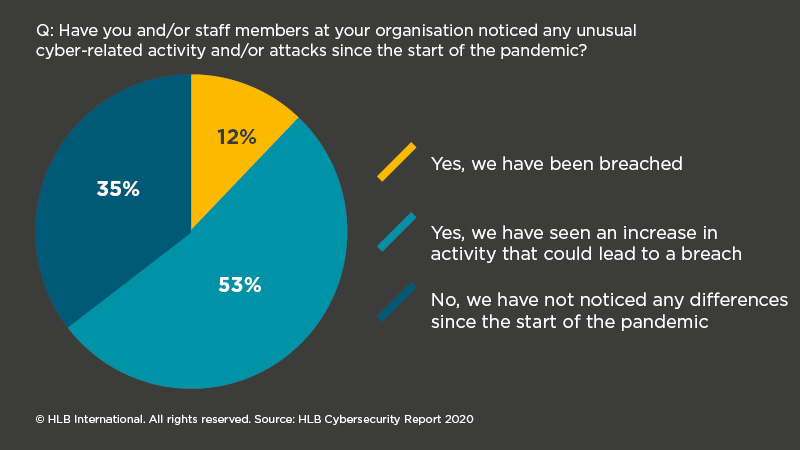
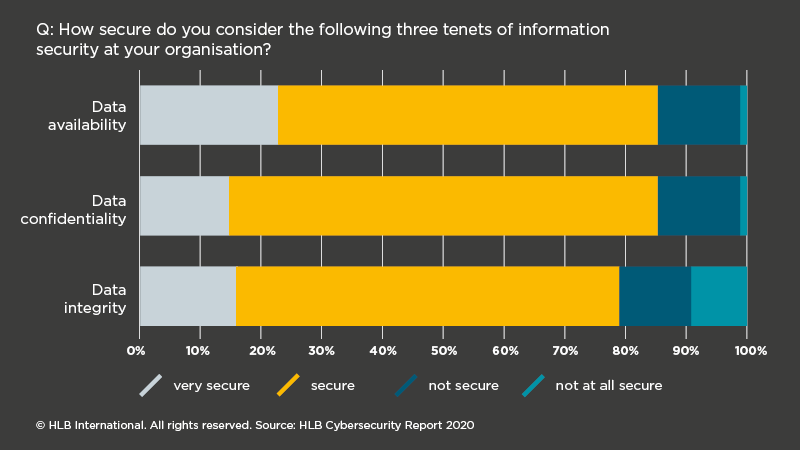
Key findings